Mission-Critical IoT Devices Receive Security That Grows and Adapts to Threats
Despite an awareness of how prevalent security breaches are becoming and how important the security of connected devices is, numerous companies still struggle to implement embedded security effectively or make informed upfront design decisions. The root causes of these issues often lie in a need for more understanding about integrating security into the infrastructure design process, resulting in a complex challenge to establish a robust defense against intrusions.
While major enterprises typically benefit from dedicated security teams tasked with ensuring device security throughout the product life cycle, smaller organizations may lack in-house expertise. Consequently, they may need help with how to approach device security, exposing them to vulnerabilities and relying heavily on their suppliers' collective security knowledge and implementation.
In these instances, Digi TrustFence® is an ideal solution.
What Is Digi TrustFence?
Digi TrustFence is a security framework that has been created to address the real-world practical challenges and limitations that businesses face in their operational practices. This framework is designed to empower organizations of all sizes, regardless of their resources and security expertise, to integrate robust device security into their products seamlessly.
Complexities abound in the realm of cryptography and information security. Implementing these concepts may seem like a formidable task, but Digi TrustFence offers a solution to simplify the process. Digi's engineers have diligently tackled these challenges, consolidating essential security features into a user-friendly and comprehensive package. Digi TrustFence stands out as an industry-leading security framework, leveraging both hardware and all software layers to streamline the often intricate task of securing connected devices.
Digi TrustFence Integrates Into A Diverse Ecosystem
Digi TrustFence seamlessly integrates into a diverse array of Digi products, ranging from cellular routers to embedded systems such as Digi XBee® RF modules, Digi XBee cellular modems, and Digi ConnectCore® System-on-Modules (SOMs).
Embedded devices - especially Internet of Things (IoT) devices - often necessitate a security approach that accommodates extended product life cycles exceeding 10 years. Similar to the way software developers rely on trusted libraries, embedded developers can turn to Digi TrustFence to establish a secure foundation without the need to design features from scratch.
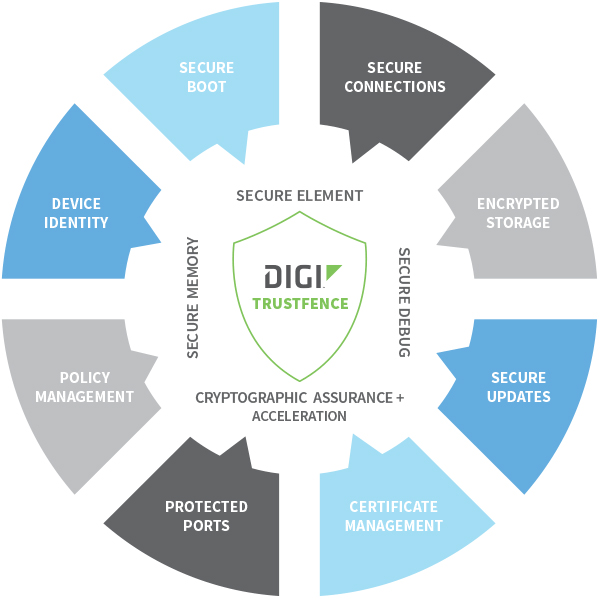
Additionally, Digi TrustFence aligns with the classic information security model to confront these challenges, emphasizing three equally critical data protection objectives:
- Confidentiality: Ensuring that only authorized individuals can access the information or device.
- Integrity: Certifying that nothing has been altered and that the information or device can be trusted as genuine.
- Availability: Guaranteeing reliable access for users, contingent upon authentication.
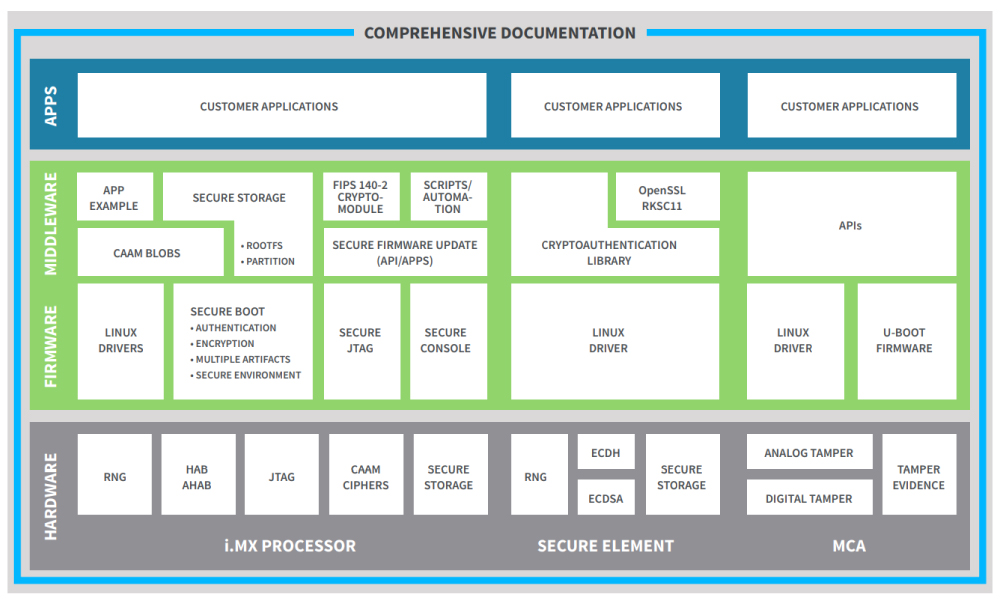
Security Features in Digi ConnectCore Modules
Adopting a "secure by design" philosophy in the interconnected landscape is crucial to safeguarding products, data, and intellectual property across multiple levels. Digi integrates a suite of security features into the ConnectCore module family to fortify against intrusion. Here are the key features incorporated into these modules:
Secure Boot
Secure Boot is a collection of authentication mechanisms designed to guarantee that only authenticated users can access a device, and exclusively certified code is permitted to execute on that device. This comprehensive approach helps safeguard against unauthorized access and ensures the integrity of the software and firmware running on the device.
No Default Password
Digi TrustFence prioritizes security by eliminating default passwords, mitigating the risk of hackers guessing administrator credentials. This proactive approach ensures that devices are not vulnerable due to predictable access credentials, enhancing overall system security.
Authenticated Firmware Upgrade
Only authorized firmware upgrades, validated by the manufacturer, are permitted under the umbrella of Digi TrustFence. This stringent measure prevents the installation of unauthorized or tampered firmware, ensuring that the device's software remains trustworthy and secure throughout its lifecycle.
External Authentication and Device Identity Management
Digi TrustFence enhances security through external authentication and robust device identity management. Leveraging certificate management and secure key storage, each device undergoes authentication before joining the network to ensure the integrity of device identities and facilitate centralized management of users.
With this system in place, password policies can be effectively enforced, eliminating the need for separate management of passwords and enhancing overall security.
Secure Element for Multi-Factor Authentication
Digi ConnectCore SOMs, featuring a Secure Element, extend security beyond traditional secure boot. The Secure Element, leveraging the crypto-authentication chip on the SOM, enables multi-factor authentication, enhancing overall security using established infrastructure.
Protected Ports
Digi ConnectCore modules provide options to secure ports and access points susceptible to manipulation, while Digi TrustFence prompts developers to address and implement crucial protections for these interfaces, fortifying the system against potential security breaches.
Secure JTAG
Most embedded devices come equipped with a JTAG interface for debugging, but if left unprotected, it can pose a significant security risk. The JTAG interface allows for halting and debugging the processor at any point, even during the crucial authentication steps during boot, providing an opportunity for attackers to interrupt and bypass authentication. Digi TrustFence provides a solution by allowing developers to switch the JTAG interface to secure mode, preventing any attacks using a hardware debugger.
Secure Console
The console is a potential vulnerability in embedded products. Attackers often attempt to locate debug UART pins, hoping to gain access to a root shell on the device. Digi recommends disabling the system console entirely in U-Boot and Linux for maximum security. If console access is necessary, Digi TrustFence offers options to enable them using a password or a GPIO pin, allowing developers to tailor security settings to specific product requirements through variable definitions.
Tamper Detection
The tamper interface serves as a means to detect unauthorized attempts to gain physical access or make modifications to a system. This interface can detect events across power modes, including power-off with battery backup, and record events into non-volatile memory. Custom countermeasures, such as instructing the system not to boot upon detecting unauthorized access, can be programmed using the Digi Embedded Yocto Board Support Package.
Secure Storage
Ensuring confidentiality is vital, especially when handling sensitive data. Digi TrustFence addresses this by using hardware-protected keys for encrypting and decrypting data, which cannot be accessed directly. This approach allows applications to protect content in flash memory, ensuring that it can only be decrypted by the i.MX processor that originally encrypted the data. Digi TrustFence simplifies the deployment of this feature, offering multiple encryption options:
- System Encryption: Encrypts the complete root filesystem, providing the highest level of security (default mode in Digi TrustFence).
- Partition Encryption: Protects specific sensitive files by setting up a dedicated encrypted partition, avoiding the performance penalty of encrypting the entire root filesystem.
- File-Specific Encryption: Allows encryption and decryption of specific files using the internal i.MX encryption key, known as CAAM blobs, for highly specific use cases.
Secure Firmware Update
In an era where security vulnerabilities abound, and new threats emerge daily, the connected nature of devices demands a robust approach to security. The secure firmware update process goes beyond merely updating a device; it ensures that the delivered image is from a known source and has not been modified to introduce malware. Enabling Digi TrustFence in a project automatically activates a secure firmware update mechanism, where the validating and programming software is a signed artifact launched by the bootloader, running entirely from RAM, to prevent tampering.
Secure Element
Digi ConnectCore SOMs feature a crypto-authentication chip, or Secure Element, enhancing the cryptographic capabilities of the main processor. This chip integrates the ECDH and ECDSA security protocols commonly used in IoT applications. The Secure Element offers hardware-based cryptographic key storage, eliminating the need to manage and store device certificates and encryption keys. Keys are securely stored in the chip, ensuring they are never exposed during cryptographic operations.
Random Number Generators (RNGs)
To ensure cryptographic systems' unpredictability, random numbers are crucial. Digi TrustFence employs a dual True Random Number Generator (TRNG) approach—one in the applications processor and a second in the Secure Element. This combines the randomness of multiple independent sources, offering a more secure implementation by not relying on a single source of entropy. The system utilizes Cryptographically Secure Random Number Generators (CSPRNGs), combining the strengths of TRNGs or HRNGs for high entropy and the efficiency of PRNGs for rapid generation and analysis.
FIPS Certification
Select Digi ConnectCore modules with TrustFence are certified to meet the Federal Information Processing Standards (FIPS) 140-2 level 1 standard. This certification is crucial for private-sector vendors seeking approval for cryptographic modules used in government departments and regulated industries. Companies can leverage existing FIPS certifications, avoiding the costly and resource-intensive process of individual FIPS integration and validation at a certified lab. The modules' FIPS 140-2 certification allows companies to obtain a certificate in their name through rebranding Digi's certificate issued by the National Institute of Standards and Technology (NIST).
Digi Remote Monitor
Digi Remote Manager provides a centralized platform for managing various aspects of connected devices. With this tool, administrators can oversee device configurations, perform firmware updates, and monitor the operational status of their devices. One major advantage is the ability to construct device configurations that minimize attack vectors, ensuring that no services directly susceptible to attacks are present on the device. By doing so, the external attack surface of the devices is significantly reduced, enhancing overall security. Additionally, the device initiates all communication for device management, establishing a highly secure and authenticated connection to Digi Remote Manager. This approach adds an extra layer of security by placing control and communication initiation in the hands of the devices being managed.
About MCA and Our CNS Team
MCA is one of the largest and most trusted integrators in the United States, offering world-class voice, data, and security solutions that enhance the quality, safety, and productivity of customers, operations, and lives. More than 65,000 customers trust MCA to provide carefully researched solutions for a safe, secure, and more efficient workplace.
Our Cellular Networking Solutions (CNS) team (formerly known as USAT) is made up of certified experts in designing and deploying fixed and mobile wireless data connectivity solutions for public and private enterprises nationwide - complete with implementation, training, proof of concept (POC), system auditing, and on-site RF surveying services with optional engineering maintenance contracts.
Our extensive catalog of world-class routers, gateways, and software designed for remote monitoring and management in even the harshest environments allows us to deliver a full suite of reliable technologies capped with a service-first approach.
Share this Post


















