What Is SD-WAN?
At its core, Software-defined WAN (SD-WAN) is about simplifying and automating your network — and about replacing manual intervention amid changing conditions with automation. It’s about making the network do more of the actual work that enables the Connected Enterprise’s increasingly fluid and flexible network Edge — the Elastic EdgeSM.
SD-WAN is an evolving technology, so characterizing an SD-WAN architecture can be difficult. How SD-WAN was defined five years ago, or even two years ago, is not necessarily how it is defined today. In fact, trying to figure out where it’s going to be a year or two from now has become an interesting thought exercise for some technology leaders.
There are, however, some fundamental SD-WAN precepts that everyone seems to agree on:
- It serves to consolidate a branch network’s functions, including routing and firewall.
- It supports multiple WAN links and uses network intelligence and policies to direct traffic across those links.
- It is managed through a cloud-based solution that can be used for centralized policy definition and troubleshooting.
And enterprises consistently cite the same top two reasons they’re considering SD-WAN:
- Reliability — Robust application and branch continuity for branch users and IoT
- Agility — A network that adapts to and supports business strategy from an infrastructure, management, and cost perspective
Until now, the benefits of SD-WAN have been confined to active-active WAN configurations. That said, recent strides in intelligent path selection capabilities combined with active-passive configurations have opened new possibilities for enterprises looking to cost-effectively leverage SD-WAN services.
This new WAN configuration — an active-dynamic WAN configuration — is a new way to think about and benefit from SD-WAN.
TABLE OF CONTENTS
What Is SD-WAN?
Active-Active WAN Configuration
Active-Passive WAN Configuration
Advantages of Active-Dynamic Configurations and SD-WAN
The Benefits of SD-WAN for Remote Access and Workforce Mobility
Software-Defined Perimeter Helps Solve Emerging IoT Challenges
What is SD-Perimeter?
Virtual Cloud Network Solutions for Mobile and Workforce Mobility Challenges
Benefits of Virtual Cloud Networks
How SD-WAN in Vehicles Works
What Is SDN?
Defining Software-Defined Networking
Software and Segregation Bring Simplicity
Abstraction and Encryption Bring Security
Programmability Brings Flexibility and Agility
Automation Brings Scalability
What Is a Software-Defined Branch?
Providing Wireless Flexibility for Primary & Failover WAN
Enabling Software-Defined Branches
Managing Various Branches From Anywhere
Replacing Many Boxes With One Solution
Improving and Simplifying Edge Security
Security, Computing, and Management for IoT at the Edge
The Future of Elastic Branch Networks
Active-Active WAN Configuration
In an active-active configuration, an organization simultaneously has two or more WAN sources connected and running at all times. Both sources are always on and available, and traffic can flow over whichever source is best optimized for the application. Should one link fail or become deteriorated, SD-WAN technology ensures that traffic is instantly and automatically routed over the other link without any data loss.
However, to execute this level of seamless and automated traffic steering, the solution must probe the network constantly and rapidly. This isn’t a problem when utilizing non-metered WAN sources such as MPLS and DSL, but for metered links such as LTE, constant probing utilizes a great amount of data, making it a costly option and, at times, counteracting some of the anticipated savings associated with software-defined networking.
Active-Passive WAN Configuration
In an active-passive configuration, only one WAN source is active at any given time. When the primary link fails, it’s possible to failover to a secondary source, but there’s a virtual certainty of data loss during this transition. However, active-passive requires far less data usage, making it a cost-effective configuration when using metered WAN links.
The differences between active-active and active-passive configurations are perhaps best illustrated by comparing a freeway to train tracks.
In an active-active configuration, the network functions like a freeway; traffic can move on or off the freeway easily and as needed based on the conditions, destination, and contents of each “vehicle” or packet.
An active-passive configuration is more like a railway system. When a “train,” or packet, leaves the track it’s on because of WAN failure, it is switched over to a secondary track — and the primary path is turned off. Only one track at a time can be used.
That said, with the right technology, the active-passive configuration can accommodate incredibly fast WAN failover and failback — facilitating intelligent routing, yielding minimal data loss, and saving a lot of money on data usage.
Advantages of Active-Dynamic Configurations and SD-WAN
Cloud-delivered network alerts are quite helpful, but often enterprises lack time to respond accordingly to all of the data they receive. Through Cradlepoint, policies automatically take care of many of the activities that in the past were strictly manual and eliminate data loss during the process. This solution combines the best parts of active-active and active-passive configurations – creating an active-dynamic WAN configuration.
Cradlepoint’s SD-WAN solution — including NetCloud Manager — enables rapidly deployed Day-1 networks that can route traffic based on bandwidth usage, application content, or preferred link to ensure maximum availability and uptime.
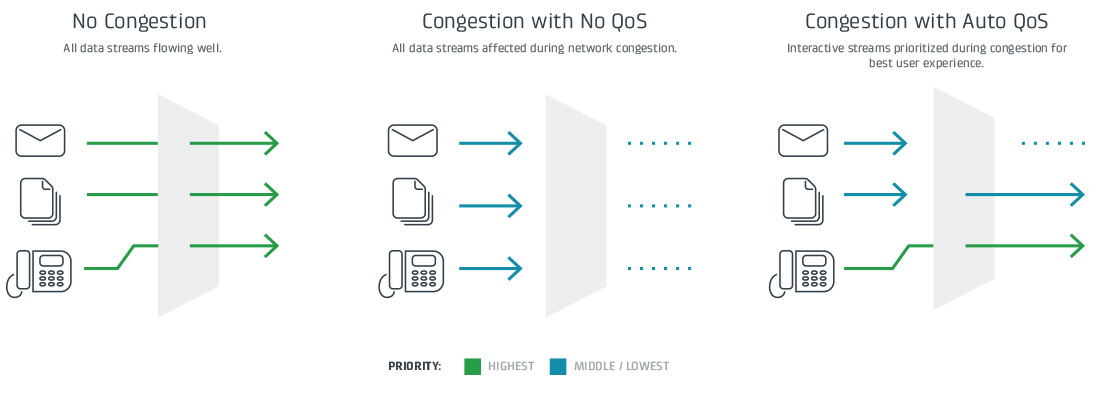
Services such as Smart WAN Selection, WAN Verify, and Auto QoS smartly assess — with minimal data usage — the health of each WAN link and its ability to run applications. IT teams can set traffic and failover policies based on high-level business intent, then rely on routers running Cradlepoint NetCloud OS to detect an outage or a deteriorated link and failover automatically.
Cradlepoint’s Auto-Tunnel enables optimized, resilient networks on top of multi-WAN solutions. This functionality automatically switches between WAN sources in sub-second speed, providing the best customer experience with essentially zero downtime. It also allows a secure VPN to be set up in a dramatically simpler fashion. Auto-Tunnel can eliminate data loss and make active-passive configurations look like an always-available connection.
The Benefits of SD-WAN for Remote Access and Workforce Mobility
Workforce mobility provides some of the biggest opportunities and challenges for enterprise networks. The bottom-line benefits of employees being able to work anywhere are clear: greater productivity during business travel, more consistent communication, workday flexibility, reduced infrastructure costs, and much more.
However, the challenges are just as clear. Employees need access to a variety of applications and documents that live either in the cloud or at the corporate data center. Meanwhile, the IT department often must use inflexible legacy architecture and hardware to provide network and application access that is highly secure no matter where employees are working from or which devices they are using.
Finding a flexible alternative to traditional VPNs is important for IT departments as workforce mobility becomes more and more prevalent.
Software-Defined Perimeter Helps Solve Emerging IoT Challenges
Enterprises, public sector organizations, and businesses of all kinds face two changing paradigms: the growing presence of the IoT, and the need to enable employee mobility. Both of these changes present exciting opportunities: More than ever, enterprises can do their best and most important work beyond the walls of the office.
At the same time, the IT team can no longer depend on a tightly controlled perimeter to keep the network secure. Today’s Network’s Edge is an Elastic Edge that is constantly expanding, contracting, and evolving. This observable shift makes it much more complex to provide users and devices with controlled but efficient access to company files, data, and applications in the cloud and at the data center.
Software-defined Perimeter (SD-P) takes a completely new approach to connecting and securing IoT devices on an organization’s network — providing IT teams with a simplified network architecture, reducing resources needed to manage the network, and offering end users a better management experience.
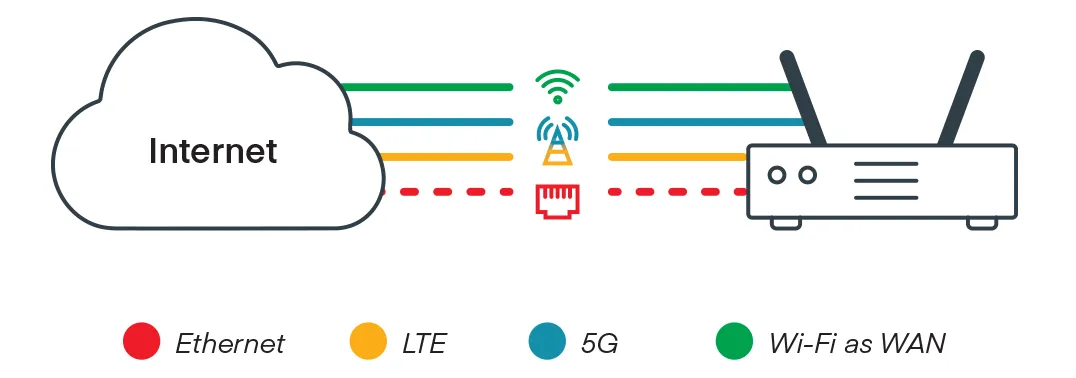
What is SD-Perimeter?
SD-P addresses many of the new networking challenges that legacy technologies only complicate. Instead of connecting networks or locations, SD-P uses a host-based approach, connecting people and things directly to the applications and resources they need. For example, a laptop that needs access to a server in the company data center will have a direct, encrypted, and hidden connection right to that server.
Different devices and users can easily be granted tailored, granular permissions without the complexity of managing an access control list. SD-P functions similarly for IoT systems. IoT devices are typically very simple, having been engineered with enough logic to perform a singular function — usually, data gathering — and not actual computing. Processing, interpreting, and distributing the data must occur elsewhere, and SD-P can provide a secure, direct connection between an IoT device and the computing device or application.
Further, SD-P actually enables the management and control of IoT devices themselves from a remote location. Thanks to the direct, LAN-like connection between the IoT devices and other computers or applications, the computing to control and manage IoT devices need not take place on-site.
Virtual Cloud Network Solutions for Mobile and Workforce Mobility Challenges
Just as remote access and workforce mobility present unique challenges, they require unique solutions. By setting up a Virtual Cloud Network through Cradlepoint’s NetCloud Engine, any IT professional can ensure users have access to important applications that live in the data center and/or cloud via one tightly controlled network.
NetCloud Engine extends SD-WAN functionality to an organization’s mobile workforce, giving employees a secure, LAN-like connection to private and public cloud apps and files from anywhere and any device. As shown in the diagram above, with NetCloud Engine running on a router at the data center and on each employee device, there is a persistent encrypted connection to a VCN overlay set up specifically for mobile access. It also seamlessly integrates with Active Directory, requiring no changes to existing infrastructure; each remote member remains “on domain” no matter its location.
NCE moves to the cloud the key functionalities that reside in traditional network architecture — such as policy control, app filtering, and NAC — without sacrificing security compliance and without needing a head-end device. Any traffic destined for any application will still flow into the data center using the NetCloud Engine client, and anything coming from the client that goes to the Internet will go directly to the Internet.
A remote worker on the road may stop in a coffee shop and browse his email on his mobile phone while waiting for the train; once he’s on the train, he may connect and work from his laptop. With NetCloud Client loaded on his mobile phone and laptop, and with access to the Active Directory server back at the data center, the Internet essentially becomes his private network. At the same time, IT administrators have policy control for micro-segmentation so they can make sure the remote employee only has access to the applications and data he needs.
Benefits of Virtual Cloud Networks
With VCNs through NetCloud Engine, enterprises can solve the pain points typically associated with legacy VPNs. Benefits of SD-WAN for remote access and mobile workforce mobility include:
- Less hardware required
- Overlay fabric provides seamless integration with legacy architecture
- More flexibility and scalability as an organization expands
- Secure atmosphere for BYOD
- Faster configurations and deployments
- Fewer IT man-hours devoted to deployments and network management
- Reduced bandwidth needs
How SD-WAN in Vehicles Works
Using an SD-WAN solution that was specially designed for vehicles allows operators to benefit from the best-performing WAN at any given time in any given location, based on preset business policies based on factors such as latency and jitter. In cities and towns, LTE might be the best path, while satellite often is the best option in remote areas. The solution automatically and instantly determines which link to use.
In situations where both LTE and satellite are viable WAN options, the in-vehicle SD-WAN solution can intelligently route traffic based on those predetermined policies. This ensures that mission-critical data is always kept on the best-performing WAN path while less-important information is relegated to separate paths whenever network conditions call for such a change.
What Is SDN?
SDN Important for Enterprise Networking, Software-defined networking (SDN) is the biggest revolution to hit enterprise networking since the Internet. It represents the latest leap forward in a non-stop progression of technological and social change that has reinvented business applications (SaaS), scale-out computing (cloud), data processing and analytics (big data), and employee work styles (mobility).
With SDN, networking finally enters the on-demand and cloud era by embracing software, virtualization, programmability, and automation. In many ways, SDN is analogous to cloud computing: part disruptive approach, part open-source and standardized tools, and part economic transformation.
Defining Software-Defined Networking
Dr. Jim Metzler from the consulting firm of Metzler and Associates defines Software-Defined Networking as follows:
“Software-Defined Networking (SDN) is an emerging architecture that is dynamic, manageable, cost-effective, and adaptable, making it ideal for the high-bandwidth, dynamic nature of today’s applications. This architecture decouples the network control and forwarding functions enabling the network control to become directly programmable and the underlying infrastructure to be abstracted for applications and network services.”
Software and Segregation Bring Simplicity
Much of the hardware-defined network architectures and technologies deployed in most enterprises today have been around for several decades. They include switches; routers; MPLS; IPsec; tiered data centers hub-and-spoke WAN topologies; border-based security; and stacks of discrete appliances at the datacenter and branch to monitor, filter, and optimize traffic.
When first introduced, the enterprise network was mostly about connecting “places,” and the employees and computing resources within them. Now, enterprises are faced with extending these legacy networks to address challenges that were never imagined when they were conceived. For example:
- Virtual machine sprawl and mobility across private and public data centers.
- Dramatically evolved threat landscape that includes social engineering, advanced persistent threats, volumetric attacks, and exploits carried out by organized actors and foreign governments.
- People wanting to work from wherever, whenever, and on whatever device they choose.
- Need to connect thousands of new “things,” such as kiosks, digital signage, HVAC controls, power meters, traffic lights, pipeline actuators, and cameras.
Trying to adapt layers of decades-old technologies to support these new requirements has made networking mind-numbingly complex, creating a schism between the dynamism, on-demand, and scale requirements of cloud, mobile, and IoT.
SDN simplifies networking for both data center and WAN deployments by moving to software many network functions that have traditionally resided in hardware, making them programmable and automatable. Additionally, SDN segregates network functions into the Control Plane and Data Plane.
The Control Plane includes functions that are dynamic and have global network relevance, such as entitlements, policy, identity, topology, and addressing. The Data Plane includes data forwarding, packet path service injection, and edge policy enforcement. This approach can dramatically simplify the network because:
- Provisioning cycles are shortened from months to minutes.
- Manual, box-by-box configurations are replaced by automation, algorithms, and instantly distributed policies and parameters (configure once, run everywhere).
- Stacks of appliances can now be virtualized, distributed, and delivered as an in-network service.
- Route selection is no longer constrained to network conditions; it can now by dynamically and externally programmed by endpoint devices and payloads, such as servers and applications.
- Virtualization Brings Economy and Reliability
- While network virtualization is not technically part of most SDN definitions, I can’t imagine many practical implementations without it. It would be akin to cloud computing without virtualization —unfathomable to most. Similar to cloud computing, network virtualization means creating a virtual network that abstracts and overlays a physical one.
This makes it possible to build multi-tenant architectures (e.g. SDN-as-a-Service), rapidly deploy new virtual networks on the fly, increase utilization of underlay networks, and enable performance optimization and high resiliency by being able to instantly migrate “network workloads” around slowdowns and failures in underlying networks.
In fact, so intertwined are the concepts of network virtualization and SDN that the VMware NSX team often has referred to their solution as a network virtualization offering rather than SDN. I’m also part of the camp that believes these two technologies are inextricable.
Abstraction and Encryption Bring Security
Enterprises today are deploying SaaS applications, cloud workloads, mobile workers, and IoT devices (e.g. collectors, sensors, and actuators) at a compounding rate. In fact, recent reports from IDC, Cisco, and Gartner predict that by 2020, 72 percent of employees will be working from primarily mobile, 56 percent of application workloads will be either SaaS or public cloud, and more than 8 billion “things” will be connected to enterprise networks. What these trends have in common is that they utilize the public Internet as their enterprise network, creating an immense new security challenge.
The traditional approach to Internet-related security has been to stop threats at the enterprise border. While essential, this is no longer adequate. That’s because apps, data, and users can reside and interact outside enterprise borders (e.g. mobile users directly accessing cloud and SaaS applications and IoT devices sending data to the cloud), and the number of insider-initiated attacks is increasing. These two simultaneous realities are making the border-driven model of security inadequate.
If we can’t rely on borders in the new connected enterprise, and we can’t privatize the entire Internet with MPLS Direct Connects, then how is this critical issue made tractable? Part of the answer is through the use of virtual overlay networks (network virtualization) with end-to-end abstraction and encryption. This approach makes it possible to build secure, private virtual networks that overlay the public Internet and underlying physical access networks, such as broadband, 4G LTE, and public WiFi hotspots.
Each virtual overlay network is encrypted end-to-end, has its own private address space that is not visible or addressable from the Internet (you can’t attack what you can’t address), does not require underlying static IP addresses, and is ephemeral. Virtual overlay networks also can have other privatized and virtualized services, such as domain naming services (DNS), network address translation (NAT), and dynamic and automatic IP address assignment.
Programmability Brings Flexibility and Agility
Automation Brings Scalability
Not only are traditional enterprise networks becoming complex, but they also require an increasing amount of skilled human capital to run them. At the same time, enterprise network endpoints are slated to grow dramatically as more mobile devices, virtual machines, and “things” are connected to them.
The only reasonable way to bridge this massive gap is through automation. SDN attributes of software, segregation, and virtualization make it possible to bring cloud-like automation to networking and achieve 10x or more factors of scale. Here are just a few of the many previously manual network tasks that can be automated in SDN networks:
- Deployment: Zero-touch provisioning and scaling of virtual networks through automation
- Configuration: Automated IP addressing, DNS, NAT, and routing tables
- Performance: Elastic capacity and dynamic load balancing of virtual network workloads
- Availability: Automated migration of virtual networks around failures within underlay networks
- As you can see, SDN is more than just a technological advancement in networking. It’s enabling a reinvention of networking in the same way that cloud technologies have led to the reinvention of computing. Stay tuned for my next blog post in this series, which will talk about how SDN is transforming the way we build, scale, and manage wide-area networks.
What Is a Software-Defined Branch?
Enterprise IT Teams Need All-in-One Network Solutions to Accommodate Constantly Evolving Branches
Software-Defined BranchIn branch locations across the world, the Digital Transformation happening in IT is stretching traditional enterprise WANs toward a breaking point. Cloud applications and IoT devices demand direct Internet access. Voice and video traffic continues to expand. Long-term and temporary branch sites are popping up everywhere, needing Internet connectivity on Day 1. Additionally, sensitive information is spread all across the WAN edge, requiring incredibly vigilant security practices.
With the rapid, ongoing adoption of technologies such as cloud, IoT, and Software-Defined Networking (SDN), meeting the needs of today’s highly connected branches — while managing an organization’s hundreds or even thousands of distributed sites — is no small task. In industries such as retail, restaurants, healthcare, education, public safety, and financial services, organizations today need a flexible, scalable Network’s Edge that can expand, contract, adapt, move, and evolve as business needs dictate.
Many enterprises are embracing cloud-managed, software-defined solutions that address the gamut of branch network necessities:
Providing Wireless Flexibility for Primary & Failover WAN
Enabling Software-Defined Branches
With companies setting their sights on the all-wireless and software-defined branch, Software-Defined WAN (SD-WAN) is increasingly important. Next-generation SD-WAN functionality optimizes path selection and traffic steering across primary and hybrid LTE WAN sources — including metered links such as LTE.
The ability to easily add access points, IoT Edge Computing, security features, and other tools and applications — and to manage it all remotely through the cloud — makes branch networks more flexible and scalable than ever.
Managing Various Branches From Anywhere
For IT teams at organizations with many branch locations, managing network traffic is about much more than ensuring uptime. They are looking for advanced analytics that provide insight into branch application and WAN, cellular, and LAN activity and utilization. Further, they need Out-of-Band Management (OOBM) features that enable remote troubleshooting.
Cradlepoint’s NetCloud Manager provides a single pane of glass through which enterprises quickly deploy, manage, and monitor their networks at geographically distributed locations — allowing them to do more with fewer resources and truck rolls.
Replacing Many Boxes With One Solution
Improving and Simplifying Edge Security
Protecting Point-of-Sale and other sensitive data remains a key concern at the branch, along with the growing challenge of shepherding network traffic that is directed toward cloud applications, video sites, and other Internet destinations. Many organizations cannot afford the time and expense associated with backhauling such high volumes of traffic to the data center.
Enterprises that leverage hardware and software with integrated Unified Threat Management can protect direct-to-Internet data with features such as app-based control, multi-zone firewall, IPS/IDS, web content filtering, Zscaler Internet Security, and OpenDNS and SIEM integrations.
Security, Computing, and Management for IoT at the Edge
Modern branches are filled with IoT devices, providing insights and ensuring new levels of operational efficiency — but also expanding the attack surface and creating new security vulnerabilities.
Cradlepoint’s NetCloud Perimeter (NCP), which uses Software-Defined Perimeter (SD-Perimeter) technology, allows IT teams to protect IoT devices at the WAN Edge by creating device-to-cloud overlay networks in just a few minutes. These perimeter-secure overlays are completely cloaked from the Internet.
Also, enterprises can use NetCloud SDK and API tools to build, deploy, connect, and secure custom Edge Computing applications on Cradlepoint routers at scale across the organization — all remotely, from a single pane of glass.
The Future of Elastic Branch Networks
About USAT
For over 25 years, USAT has provided mobile communications solutions for various retail applications across the USA. With our extensive catalog of world-class routers, gateways, and software designed for remote monitoring and management in even the harshest environments — you can count on us to get and keep you connected.
Better mobile connectivity translates to less manual equipment maintenance, reduced downtime, and an overall increase in your business’s ROI. Contact the experts at USAT to learn how our wireless networking solutions can help meet your organization’s exacting needs.
Share this Post















