Remote Desktop Protocol Requires Significant Security Obligations
Many professionals seek to implement the Remote Desktop Protocol (RDP) as a key component in their industrial environments to enable remote monitoring, configuration, and troubleshooting of essential systems like PLCs, HMIs, and SCADA servers. RDP, a network communication protocol developed by Microsoft, allows users to connect remotely to other computers, making it a widely accessible and standardized tool. However, this ease of use comes with significant security obligations.
An unsecured RDP connection can severely impact operations, halt production lines, and compromise safety measures in the current cybersecurity landscape.
RDP Security Risks
RDP introduces a range of security vulnerabilities, including:
Expanded Network Attack Surfaces
Network ports must be left open to enable RDP functionality, which can expose devices to threats. Unfortunately, RDP often comes with weak default settings, such as disabled Network Level Authentication (NLA) and easily guessable passwords, making it susceptible to brute-force attacks.
Unrestricted Access
By default, RDP permits connections from any external IP address, significantly increasing the attack surface and the potential for unauthorized access.
Lateral Movement
Once a system is compromised, attackers can use it as a pivot point to access other valuable assets within the network.
Traditional Processes for RDP Security Aren’t Enough
Traditionally, security experts have advised implementing the following steps to secure your RDP access:
- Activate Network Level Authentication (NLA): This step enhances security by requiring user verification before establishing a connection.
- Limit access and ports: Restrict RDP access to specific IP addresses and ports to minimize the chances of unauthorized attempts reaching your system.
- Use robust passwords and Multi-Factor Authentication (MFA): Employing strong, complex passwords and MFA creates significant obstacles for attackers, making it much harder to penetrate your defenses.
- Keep systems updated: Regularly patching vulnerabilities is essential, as outdated software can present easy opportunities for exploits.
- Evaluate alternatives: Look into secure alternatives such as VPNs or dedicated remote access solutions, particularly in high-risk scenarios. Typically, organizations do not allow RDP access without a VPN. However, the complexity and cost of VPNs can pose their own issues, and recent security flaws have sometimes rendered VPN protections ineffective. This becomes especially concerning if the RDP setup is overly permissive, relying solely on VPN protection.
Unfortunately, none of these measures are foolproof. Open network attack surfaces persist, and attackers can move laterally from one system to another. While VPNs encrypt your data, they can also be slow, unreliable, and raise privacy concerns depending on the provider and user practices.
The optimal solution for securing your remote systems involves addressing all security issues while still permitting full RDP access. This means no attack surfaces (no exposed ports), complete data encryption, access granted only to those who are cryptographically authenticated, and no lateral movement (unless explicitly authorized).
Sound impossible? It's not with SSH No Ports.
Fortify Your RDP Security with SSH No Ports
Atsign's SSH No Ports solution mitigates these risks by establishing a secure tunnel with an encrypted control plane. Think of it as a dedicated pathway for your data, safeguarded by unique keys securely stored on your devices.
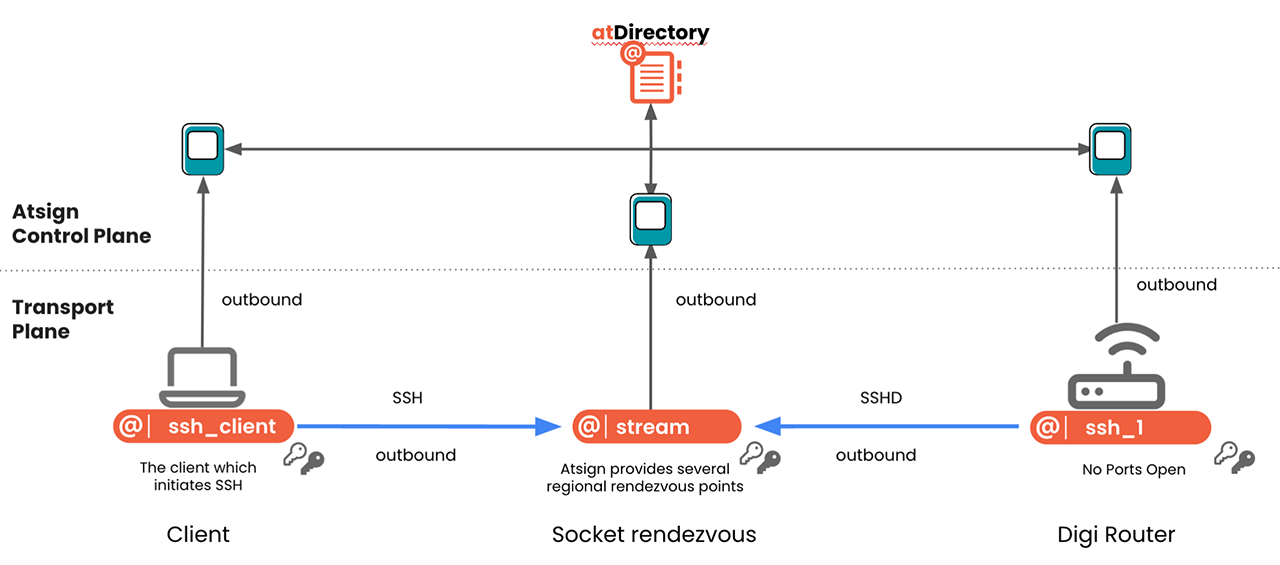
Enhanced RDP Security with SSH No Ports
Unlike traditional methods, SSH No Ports eliminates the complexity of managing firewall configurations and multiple passwords. This simplification enhances security management and optimizes access control.
- No exposed ports: SSH No Ports eliminates the necessity for exposed network ports, which attackers often target. This removal significantly enhances the security of your RDP environment.
- End-to-end encryption: All data passing through the tunnel is encrypted using edge-cut keys, ensuring confidentiality even if intercepted.
- Cryptographic authentication: Every access attempt undergoes rigorous cryptographic validation, preventing unauthorized users and enhancing overall system security.
- Reduced lateral movement: Implementing SSH No Ports across your network devices effectively minimizes the risk of lateral movement.
Using RDP with SSH No Ports
Using SSH No Ports ensures seamless RDP access with these straightforward steps:
- Establish the secure tunnel: The SSH No Ports client sets up an encrypted tunnel to the remote RDP server, ensuring a secure connection.
- Utilize familiar RDP: Your existing RDP client securely connects through this encrypted tunnel, offering the familiar RDP experience you know.
Beyond RDP: A Versatile Solution
SSH No Ports offers benefits beyond RDP, enabling secure connections for various TCP protocols like VNC, HTTPS, ICA, and more.
Simplified Deployment with Digi Routers
Deploying SSH No Ports consists of two essential components:
- SSH No Ports Daemon: Installed on your Digi IX40 or Digi EX50 router, running within a secure Digi Container to enhance protection.
- SSH No Ports Client: An easy-to-install client for Linux, MacOS, and Windows platforms.
With SSH No Ports, you can elevate security and user experience for remote access. This solution eliminates exposed ports, employs strong encryption, supports various protocols seamlessly, and simplifies deployment for comprehensive usability.
About MCA and Our CNS Team
MCA is one of the largest and most trusted integrators in the United States, offering world-class voice, data, and security solutions that enhance the quality, safety, and productivity of customers, operations, and lives. More than 65,000 customers trust MCA to provide carefully researched solutions for a safe, secure, and more efficient workplace.
Our Cellular Networking Solutions (CNS) team (formerly known as USAT) is made up of certified experts in designing and deploying fixed and mobile wireless data connectivity solutions for public and private enterprises nationwide - complete with implementation, training, proof of concept (POC), system auditing, and on-site RF surveying services with optional engineering maintenance contracts.
Our extensive Digi catalog of world-class routers, gateways, and software designed for remote monitoring and management in even the harshest environments allows us to deliver a full suite of reliable technologies capped with a service-first approach.
Share this Post













