Sierra Wireless is pleased to announce that they have officially released AM/AMM 2.17.5, a major release of the AirLink Manager Platform. The product was released on October 20, 2023.
This release introduces significant new improvements for administrators of the AMM platform. It also serves as a foundational release, redefining the approach for upgrading the server in the future. Once 2.17.5 is installed, any future upgrades can be completed by end users, using a new menu option in the administrative UI. Direct support from the Sierra Wireless Customer Support Team will no longer be required. Sierra Wireless expects that this new self-serve upgrade capability will allow us to make more frequent AM/AMM releases, keeping all customers more secure.
To continue to improve the security posture of the AM/AMM platform, new security patches have been integrated.
Here are highlights of the new features in this release:
- Self Serve Upgrade AMM: AM/AMM 2.17.5 redefines the approach for upgrading the server. To upgrade to 2.17.5, only one command is executed in a Linux terminal window. See Upgrade to 2.17.5 for more details. Once 2.17.5 is installed, any future upgrades will be completed using a new menu option in the administrative UI. Refer to System Upgrade for more details.
- System Configuration GUI: AM/AMM 2.17.5 provides a new user interface option that will allow the administrator to configure the system or application settings. Refer to System Configuration for more details.
- High Availability Configuration GUI: AM/AMM 2.17.5 introduces a new user interface menu option for configuring an HA pair, including HA setup, role swapping and teardown. Refer to HA Configuration for more details.
- Minor Feature Enhancements
- Admin Menu Redesign: The user interface admin dropdown menu has been redesigned to streamline and simplify the administrative functions of the AMM.
- Admin Privilege: A new privilege has been added when defining an AMM user. The Admin privilege defines the user to have administrative privileges over other users and access to all admin features.
- Remote User Group Support with Microsoft LDAP Schema: AM/AMM 2.17.5 enhances the LDAP search operation by incorporating “search base” and “search filter”. This allows you to define the scope and criteria for your search, thereby enabling a more efficient retrieval of a specific entry.
- System Certificate Upload GUI: AM/AMM 2.17.5 has introduced the capability to upload a system certificate via a new user interface menu option.
- Group API: This release adds a new API endpoint to allow customers to retrieve the latest stats data from a fleet of devices in a Group. This reduces the number of API calls required when a user queries the latest stats. AM/AMM now supports the Group as a query parameter.
- System ID: The System ID for the AMM server is now displayed in the Help > About menu.
Please note that all AM/AMM documentation is now published online rather than via PDFs. The updated documentation for the release is published here: https://source.sierrawireless.com/airvantage/amm/
Similarly, the release notes are also published online on the Source: https://source.sierrawireless.com/airvantage/amm/reference/releasenotes/
Release Notes for AM/AMM 2.17.5
1 Release Information
AirLink Manager (AM)/AirLink Mobility Manager (AMM) 2.17.5 is a minor release of the AirLink Manager Platform that introduces significant new improvements for administrators of the AMM platform. It also serves as a foundational release, redefining the approach for upgrading the server in the future. Once 2.17.5 is installed, any future upgrades can be completed by end users, using a new menu option in the administrative UI. Direct support from the Sierra Wireless Customer Support Team will no longer be required. We expect that this new self-serve upgrade capability will allow us to make more frequent AM/AMM releases, keeping all customers more secure.
To continue to improve the security posture of the AM/AMM platform, new security patches have been integrated. The AMM 2.17.5 release is generally available and ready for install.
- 1.1 Released Version
- AM/AMM 2.17.5 was released to General Availability on Oct 20, 2023.
- AM/AMM 2.17.5 was released to General Availability on Oct 20, 2023.
- 1.2 Platform Support
- AM/AMM 2.17.5 has been tested on Dell R250 and R650 servers and on VMWare ESXi 6 and later.
- AM/AMM 2.17.5 has been tested on Dell R250 and R650 servers and on VMWare ESXi 6 and later.
- 1.3 Browser Support
- AMM 2.17.5 has been tested on Google Chrome, Firefox, and Microsoft Edge. Users that attempt to use a browser that is not supported will get a warning and may experience some issues.
- AMM 2.17.5 has been tested on Google Chrome, Firefox, and Microsoft Edge. Users that attempt to use a browser that is not supported will get a warning and may experience some issues.
- 1.4 Sierra Wireless Gateway Support
- The following table shows the minimum software version needed on the gateways to be used with AMM 2.17.5.
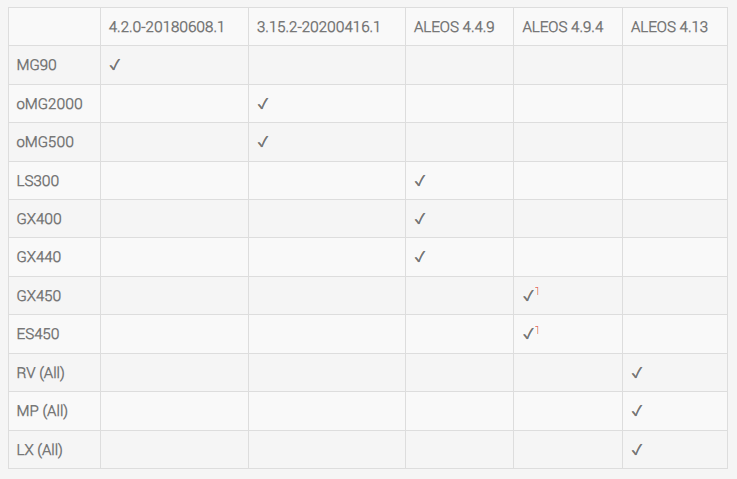
1 : There is no support for the management tunnel for ALEOS 4.9 (GX450/ES450). Please contact Technical Support for more information.
2 Key Features and Enhancements
- 2.1 Self Serve Upgrade AMM
AM/AMM 2.17.5 redefines the approach for upgrading the server. To upgrade to 2.17.5, only one command is executed in a Linux terminal window. See Upgrade to 2.17.5 for more details. Once 2.17.5 is installed, any future upgrades will be completed using a new menu option in the administrative UI. Refer to System Upgrade for more details. - 2.2 System Configuration GUI
AM/AMM 2.17.5 provides a new user interface option that will allow the administrator to configure the system or application settings. Refer to System Configuration for more details. - 2.3 High Availability Configuration GUI
AM/AMM 2.17.5 introduces a new user interface menu option for configuring an HA pair, including HA setup, role swapping and teardown. Refer to HA Configuration for more details. - 3 Minor Feature Enhancements
3.1 Admin Menu Redesign
The user interface admin dropdown menu has been redesigned to streamline and simplify the administrative functions of the AMM. - 3.2 Admin Privilege
A new privilege has been added when defining an AMM user. The Admin privilege defines the user to have administrative privileges over other users and access to all admin features. - 3.3 Remote User Group Support with Microsoft LDAP schema
AM/AMM 2.17.5 enhances the LDAP search operation by incorporating “search base” and “search filter”. This allows you to define the scope and criteria for your search, thereby enabling a more efficient retrieval of a specific entry. - 3.4 System Certificate Upload GUI
AM/AMM 2.17.5 has introduced the capability to upload a system certificate via a new user interface menu option. - 3.5 Group API
This release adds a new API endpoint to allow customers to retrieve the latest stats data from a fleet of devices in a Group. This reduces the number of API calls required when a user queries the latest stats. AM/AMM now supports the Group as a query parameter. - 3.6 System ID
The System ID for the AMM server is now displayed in the Help > About menu.
4.0 Addressed Problems
Customer Reported Field Issues
- 11683 | Vehicle Diagnostic report template created on 2.16 or older versions contains data that is incompatible to 2.17.2 or above releases. After upgrading to 2.17.5, AMM will delete the old generated reports and fix the template.
- 11667 | Unprivileged user is able to add, delete and change other users
- 11590 | CSV date format unexpected change
- 11524 | setupNewSdbAsDataDrive.sh script fails with drives larger than 2TB
- 11523 | setupNewSdbAsDataDrive.sh script unable to process previously used data drive
- 11427 | Upgrade script verifies minimum RAM requirement
- 11407 | Remote user group feature incompatible with standard Microsoft LDAP schema
- 11315 | New HFSN PID added since 2.17.3
- 11178 | Satellite view doesn’t work in some map reports
- 11174 | Require HTTPS URL support for legacy ALEOS firmware update
- 11164 | Invalid image links on emailed reports from HTTPS only AMM
- 9670 | Configuration Control Page - ‘Linked config templates’ window - Linked template missing the “Out Of Sync” tag.
- 8782 | Pre-install open-vm-tools to AMM VMware image
Security Vulnerabilities
CVE-2023-38408
CVE-2023-32233
CVE-2023-31436
CVE-2023-30456
CVE-2023-21980
CVE-2023-29007
CVE-2023-28772
CVE-2023-28708
CVE-2023-28466
CVE-2023-28464
CVE-2023-2828
CVE-2023-27533
CVE-2023-27522
CVE-2023-27320
CVE-2023-26604
CVE-2023-26545
CVE-2023-26242
CVE-2023-2603
CVE-2023-25690
CVE-2023-25652
CVE-2023-28708
CVE-2023-24998
CVE-2023-24329
CVE-2023-23946
CVE-2023-22809
CVE-2023-22602
CVE-2023-22743
CVE-2023-22602
CVE-2023-21980
CVE-2023-21930
CVE-2023-2124
CVE-2023-2007
CVE-2023-1838
CVE-2023-1829
CVE-2023-1513
CVE-2023-1380
CVE-2023-1281
CVE-2023-1252
CVE-2023-1118
CVE-2023-1077
CVE-2023-0461
CVE-2023-0386
CVE-2023-0286
CVE-2023-0266
CVE-2023-0215
CVE-2022-48303
CVE-2022-45934
CVE-2022-45919
CVE-2022-45886
CVE-2022-45885
CVE-2022-45884
CVE-2022-45143
CVE-2022-45061
CVE-2022-4450
CVE-2022-43995
CVE-2022-43945
CVE-2022-43750
CVE-2022-43680
CVE-2022-42898
CVE-2022-42896
CVE-2022-42252
CVE-2022-42004
CVE-2022-42003
CVE-2022-41966
CVE-2022-41953
CVE-2022-41903
CVE-2022-4139
CVE-2022-41222
CVE-2022-40674
CVE-2022-40664
CVE-2022-40304
CVE-2022-40303
CVE-2022-40153
CVE-2022-3970
CVE-2022-39260
CVE-2022-39189
CVE-2022-38178
CVE-2022-38177
CVE-2022-3775
CVE-2022-37434
CVE-2022-36946
CVE-2022-36883
CVE-2022-36882
CVE-2022-36760
CVE-2022-3594
CVE-2022-3565
CVE-2022-3545
CVE-2022-3515
CVE-2022-34305
CVE-2022-34169
CVE-2022-32532
CVE-2022-32250
CVE-2022-32207
CVE-2022-3239
CVE-2022-31813
CVE-2022-31692
CVE-2022-31012
CVE-2022-30948
CVE-2022-30947
CVE-2022-30594
CVE-2022-30556
CVE-2022-3028
CVE-2022-29885
CVE-2022-29581
CVE-2022-29404
CVE-2022-29154
CVE-2022-28893
CVE-2022-28615
CVE-2022-28390
CVE-2022-28377
CVE-2022-2795
CVE-2022-27782
CVE-2022-27781
CVE-2022-27406
CVE-2022-27405
CVE-2022-27404
CVE-2022-26377
CVE-2022-2601
CVE-2022-25315
CVE-2022-25314
CVE-2022-25265
CVE-2022-25236
CVE-2022-25235
CVE-2022-2509
CVE-2022-24975
CVE-2022-24765
CVE-2022-23943
CVE-2022-23852
CVE-2022-23521
CVE-2022-23308
CVE-2022-23307
CVE-2022-23305
CVE-2022-23302
CVE-2022-22978
CVE-2022-22827
CVE-2022-22826
CVE-2022-22825
CVE-2022-22824
CVE-2022-22823
CVE-2022-22822
CVE-2022-22721
CVE-2022-22719
CVE-2022-22576
CVE-2022-2196
CVE-2022-21824
CVE-2022-2048
CVE-2022-1943
CVE-2022-1927
CVE-2022-1897
CVE-2022-1785
CVE-2022-1586
CVE-2022-1048
CVE-2022-0778
CVE-2021-46877
CVE-2021-46143
CVE-2021-46101
CVE-2021-45960
CVE-2021-44790
CVE-2021-44531
CVE-2021-43859
CVE-2021-41303
CVE-2021-4104
CVE-2021-40633
CVE-2021-40330
CVE-2021-39154
CVE-2021-39153
CVE-2021-39152
CVE-2021-39151
CVE-2021-39150
CVE-2021-39149
CVE-2021-39148
CVE-2021-39147
CVE-2021-39146
CVE-2021-39145
CVE-2021-39144
CVE-2021-38185
CVE-2021-38166
CVE-2021-37713
CVE-2021-37712
CVE-2021-37701
CVE-2021-3737
CVE-2021-3712
CVE-2021-3711
CVE-2021-3518
CVE-2021-3517
CVE-2021-3450
CVE-2021-3444
CVE-2021-32804
CVE-2021-32803
CVE-2021-32749
CVE-2021-31566
CVE-2021-3156
CVE-2021-29657
CVE-2021-29505
CVE-2021-29468
CVE-2021-26934
CVE-2021-26930
CVE-2021-26690
CVE-2021-26117
CVE-2021-28861
CVE-2021-23240
CVE-2021-23177
CVE-2021-22946
CVE-2021-22926
CVE-2021-22119
CVE-2021-22112
CVE-2021-21351
CVE-2021-21350
CVE-2021-21349
CVE-2021-21348
CVE-2021-21347
CVE-2021-21346
CVE-2021-21345
CVE-2021-21344
CVE-2021-21343
CVE-2021-21342
CVE-2021-21341
CVE-2021-21300
CVE-2021-20233
CVE-2021-20190
CVE-2020-9548
CVE-2020-9547
CVE-2020-9546
CVE-2020-9493
CVE-2020-8840
CVE-2020-5398
CVE-2020-36518
CVE-2020-36189
CVE-2020-36188
CVE-2020-36187
CVE-2020-36186
CVE-2020-36185
CVE-2020-36184
CVE-2020-36183
CVE-2020-36182
CVE-2020-36181
CVE-2020-36180
CVE-2020-36179
CVE-2020-35728
CVE-2020-35514
CVE-2020-35492
CVE-2020-35491
CVE-2020-35490
CVE-2020-2981
CVE-2020-27779
CVE-2020-27786
CVE-2020-26945
CVE-2020-26258
CVE-2020-26217
CVE-2020-25649
CVE-2020-25647
CVE-2020-25645
CVE-2020-25632
CVE-2020-24750
CVE-2020-24616
CVE-2020-1967
CVE-2020-1957
CVE-2020-17523
CVE-2020-17510
CVE-2020-14697
CVE-2020-14678
CVE-2020-14663
CVE-2020-14372
CVE-2020-14195
CVE-2020-14062
CVE-2020-14061
CVE-2020-14060
CVE-2020-13933
CVE-2020-13933
CVE-2020-11989
CVE-2020-11620
CVE-2020-11619
CVE-2020-11113
CVE-2020-11112
CVE-2020-11111
CVE-2020-10969
CVE-2020-10968
CVE-2020-10713
CVE-2020-10683
CVE-2020-10673
CVE-2020-10672
CVE-2020-10650
CVE-2019-9003
CVE-2019-5482
CVE-2019-5481
CVE-2019-5443
CVE-2019-2822
CVE-2019-2800
CVE-2019-20330
CVE-2019-19956
CVE-2019-19234
CVE-2019-19232
CVE-2019-17571
CVE-2019-17531
CVE-2019-16943
CVE-2019-16942
CVE-2019-15917
CVE-2019-15903
CVE-2019-12422
CVE-2019-10172
CVE-2019-10086
CVE-2019-0145
CVE-2018-25032
CVE-2018-20843
CVE-2018-16884
CVE-2018-16395
CVE-2016-3440
CVE-2016-3092
CVE-2016-1000031
CVE-2015-7538
CVE-2015-7537
CVE-2015-6420
CVE-2015-5325
CVE-2006-20001
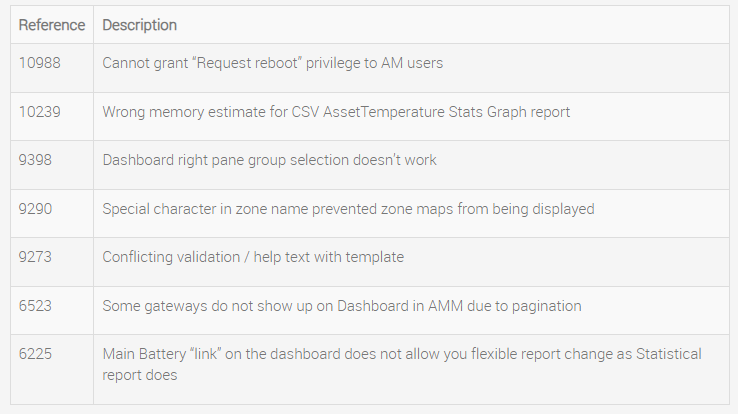
5.0 Outstanding Problems
About MCA and Our CNS Team
MCA is one of the largest and most trusted integrators in the United States, offering world-class voice, data, and security solutions that enhance the quality, safety, and productivity of customers, operations, and lives. More than 65,000 customers trust MCA to provide carefully researched solutions for a safe, secure, and more efficient workplace.
Our Cellular Networking Solutions (CNS) team (formerly known as USAT) is made up of certified experts in designing and deploying fixed and mobile wireless data connectivity solutions for public and private enterprises nationwide - complete with implementation, training, proof of concept (POC), system auditing, and on-site RF surveying services with optional engineering maintenance contracts.
Our extensive catalog of world-class routers, gateways, and software designed for remote monitoring and management in even the harshest environments allows us to deliver a full suite of reliable technologies capped with a service-first approach.
Share this Post













